Security Onion 20111229 is now available! This resolves the following issues:
Thanks to Karolis for his work on integrating PADS into the distro!
Notes
- The PADS configuration file (/etc/nsm/SENSOR-NAME/pads.conf) contains a "network" variable which defaults to:
192.168.0.0/16,10.0.0.0/8,172.16.0.0/12
You will need to change this variable if you're monitoring public IP space. - The new process watchdog runs every 5 minutes and will restart any sensor process that has crashed. It will move the process's old log file to PROCESS.log.TIMESTAMP so that you can determine why the process crashed.
New Users
New users can download and install the 20111103 ISO image using the instructions here. The step marked "Install Security Onion updates" will automatically install this update.
In-place Upgrade
Existing Security Onion users can perform an in-place upgrade using the following command (if you're behind a proxy, remember to set your proxy variables as described in the FAQ):
New users can download and install the 20111103 ISO image using the instructions here. The step marked "Install Security Onion updates" will automatically install this update.
In-place Upgrade
Existing Security Onion users can perform an in-place upgrade using the following command (if you're behind a proxy, remember to set your proxy variables as described in the FAQ):
sudo -i "curl -L http://sourceforge.net/projects/security-onion/files/security-onion-upgrade.sh > ~/security-onion-upgrade.sh && bash ~/security-onion-upgrade.sh"Note that the upgrade script is cumulative and will upgrade any older version of Security Onion to the most recent version (including any updates in between).
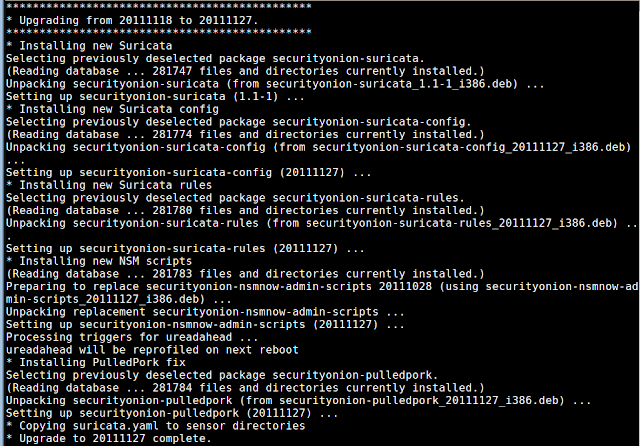
Screenshots
 |
| Upgrade Process |
 |
| PADS events in Sguil |
If you're a fan of Security Onion, please vote for it for 2011 Toolsmith Tool of the Year!
http://holisticinfosec.blogspot.com/2011/12/choose-2011-toolsmith-tool-of-year.html