Issue 134 - Upgrade Suricata to 1.1
Issue 153 - When IDS Engine is Suricata, PulledPork needs to download Suricata version of ET rules
If you are already using Suricata and have customized your suricata.yaml file, please note that it will be backed up to /nsm/backup/20111127/NAME-OF-SENSOR/ and then overwritten with the new config file. Please copy any of your customizations (HOME_NET, etc.) from /nsm/backup/20111127/NAME-OF-SENSOR/suricata.yaml to the production copy /etc/nsm/NAME-OF-SENSOR/suricata.yaml.
New Users
New users can download and install the 20111103 ISO image using the instructions here. The step marked "Install Security Onion updates" will automatically install this update.
In-place Upgrade
Existing Security Onion users can perform an in-place upgrade using the following command (if you're behind a proxy, remember to set your proxy variables as described in the FAQ):
sudo -i "curl -L http://sourceforge.net/projects/security-onion/files/security-onion-upgrade.sh > ~/security-onion-upgrade.sh && bash ~/security-onion-upgrade.sh"
Note that the upgrade script is cumulative and will upgrade any older version of Security Onion to the most recent version (including any updates in between).
Switching to Suricata
If you're currently running Snort and would like to switch to Suricata, use the following commands to stop Snort, change the ENGINE variable in the config file, and then run PulledPork to download the Suricata-specific ruleset (if running Emerging Threats rules):
sudo nsm_sensor_ps-stop --only-snort-alert
sudo sed -i 's|ENGINE=snort|ENGINE=suricata|g' /etc/nsm/securityonion.conf
sudo /usr/local/bin/pulledpork_update.sh
Screenshots
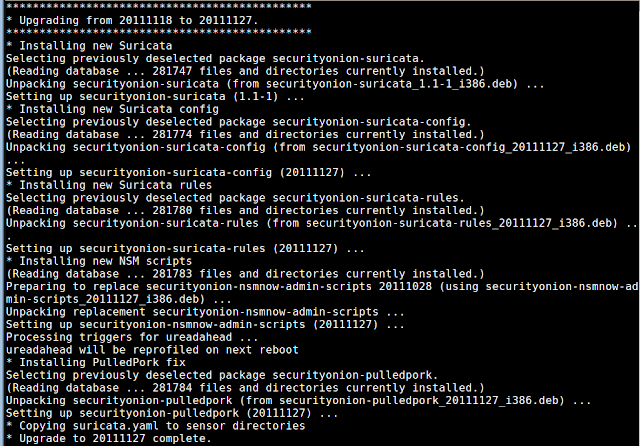 |
| Upgrade Process |
No comments:
Post a Comment