At Security Onion Conference 2022, we showed a sneak peek of Security Onion 2.4: https://blog.securityonion.net/2022/10/sneak-peek-at-security-onion-24.html
We have been overwhelmed by the excitement from our community and customers about Security Onion 2.4!
Today, we are excited to release the first Beta version of Security Onion 2.4. This release builds on the success of 2.3 but is easier to install, configure, and maintain. In addition, it's more powerful yet more streamlined!
New Features
Let’s start by talking about some of the many new features in Security Onion 2.4!
Configuration Interface
With the introduction of the configuration interface, we hope to reduce the overall time spent to manage and administer the grid. The goal is to make editing files at the command line a thing of the past. The configuration interface will help lower the barrier of entry for new users to the platform as well as be a nice convenience for our more seasoned users.
Enhanced Grid Status Interface
In addition to the configuration interface, we’ve also enhanced the SOC Grid page to give you more information about the status of your grid.
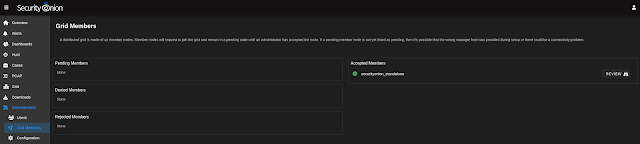
New Grid Members Interface
There is a new Grid Members interface used to review and accept new nodes that attempt to join the grid.
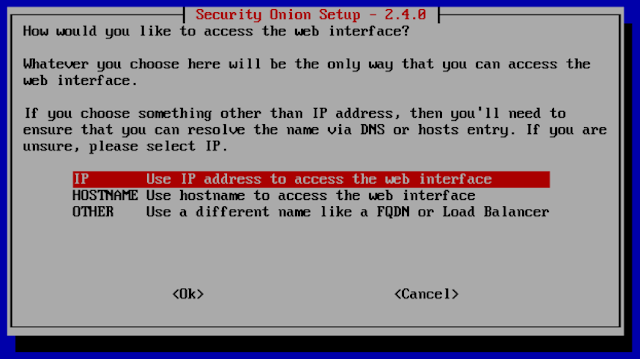
Simplified Setup
The installer has been greatly simplified and configuring new members of the grid will take place in the configuration interface. This removes the need for the soremote account and ssh access to the manager.
Elastic Agent and Elastic Fleet
Our primary endpoint agent will be Elastic Agent. It replaces osquery, Beats, and Wazuh and is easily managed in Elastic Fleet, giving more control over upgrades. Users will also be able to deploy agents in standalone (unmanaged) mode if they choose to do so.
Security Onion Virtual Appliance based on Rocky Linux 9
When we were laying out features for Security Onion 2.4, we really wanted to shift the focus away from the OS and more into features that help our users find evil. We felt that we needed to shift to more of a virtual appliance model to allow us to continue to grow and scale to the needs of the future. We are basing this new appliance model on Rocky Linux 9. This change will allow us to deliver features faster and simplify support of the platform. Rocky Linux 9 has an EOL date of March 2032 allowing us to continue to innovate on the platform for years to come. Users will be able to install Security Onion either from our ISO image or on top of a minimal installation of Rocky Linux 9. Below we explain how this will impact Ubuntu-based deployments.
Simplified Updates
For this new virtual appliance model, all packages will be distributed from the manager similar to the current Airgap mode. You can optionally override the package source to some other source which hosts specific signed packages. In non-Airgap deployments, the manager or repo will sync daily with the upstream Security Onion repo to ensure updates are downloaded from the Internet. Airgap deployments will continue to pull their updates from the latest ISO image as they do in 2.3.
Improved Health Metric Visualizations
Security Onion 2.4 includes InfluxDB 2 and some improved health metric visualizations.
Component Changes in Security Onion 2.4
Security Onion 2.4 has some major changes, including components that have been retired or are being phased out:
Ubuntu support
Wazuh
FleetDM
Dedicated osquery agents
Filebeat for SO components
Phasing Out Support for Ubuntu
Back in 2009, the first release of Security Onion was based on Ubuntu 9.04 and we have continued to support Ubuntu through Security Onion 2.3. Since Security Onion 2.4 is shifting to more of an appliance model based on Rocky Linux 9 (as described above), we are phasing out support for Ubuntu. Users running a large distributed grid of Ubuntu 20.04 nodes will be able to gradually migrate those nodes to the new appliance structure as long as the manager runs Rocky Linux 9. We will release more details on this as we finalize the process.
Endpoint Agent Changes
As mentioned above, our primary endpoint agent will be Elastic Agent:
- Since Elastic Agent has osquery built in, it will be taking the place of the current osquery agent.
- Security Onion 2.4 will also use the Elastic Agent to send alerts and metadata from the sensors to the back end, replacing the current Filebeat agent.
- Users will be able to manage all of their Elastic Agents using Elastic Fleet in Kibana.
- Since Elastic Agent covers most of the Wazuh use cases used in Security Onion, Wazuh is being removed as well.
Known Issues
Here are some known issues that should be resolved in later releases:
You cannot do an in-place upgrade from 2.3 to 2.4. We are still investigating the feasibility of migrating data.
You must perform a new installation of Rocky Linux 9 Minimal and have full Internet access. We hope to have a 2.4 ISO image in a future release.
Upgrades from this 2.4 Beta release to anything else will not be supported. Starting in RC2 we will support soup to upgrade 2.4 grids.
Airgap mode is not supported at this time. This is due to a 3rd party dependency but will be supported in RC1.
Ubuntu 20.04 support is not available until RC1. This has to do with a 3rd party dependency.
Elastic agents will connect directly to the Elasticsearch cluster. Future releases will have the Elastic agents sending their data to Logstash similar to how the data pipeline works in version 2.3.
ATT&CK Navigator doesn’t work correctly yet.
so-import-evtx imports logs but they don't get parsed correctly.
The following installation modes are NOT supported at this time:
Heavy Node
Receiver Node
Analyst Workstation
Dedicated Elastic Fleet Node
Transition from 2.3 to 2.4
When we release the final version of Security Onion 2.4, we will announce an End Of Life (EOL) date for Security Onion 2.3. Security Onion 2.3 will continue to receive security patches and priority bug fixes until it reaches EOL.
Documentation
You can find 2.4 documentation at:
https://docs.securityonion.net/en/2.4/
Documentation is always a work in progress. If you find documentation that needs to be updated, please let us know as described in the Feedback section below.
Warnings and Disclaimers
This is Beta software. It is not a finished product.
Beta software is not officially supported for production usage.
Ask your doctor if Beta software is right for you.
- Using Beta software can cause a disruption in the space time continuum.
If it breaks, you get to keep both pieces!
Enough warnings and disclaimers? Let’s go!
Installation
Our Security Onion 2.4 ISO image is not quite ready yet so for now you'll need to download Rocky Linux 9 Minimal: https://download.rockylinux.org/pub/rocky/9/isos/x86_64/Rocky-9.1-x86_64-minimal.iso
Then check the checksum: https://download.rockylinux.org/pub/rocky/9/isos/x86_64/CHECKSUM
Next, install Rocky Linux 9 and start our Security Onion installation as shown here:
https://docs.securityonion.net/en/2.4/installation.html#installation-on-rocky-linux-or-ubuntu
Once you've installed Rocky Linux 9 Minimal and started our Setup wizard, we highly recommend that you start with a simple IMPORT installation as shown here:
https://docs.securityonion.net/en/2.4/first-time-users.html
Once you have verified proper IMPORT installation, you can then try EVAL, STANDALONE, and DISTRIBUTED deployments as described here:
https://docs.securityonion.net/en/2.4/configuration.html
Questions, Problems, and Feedback
If you have any questions or problems relating to Security Onion 2.4, please use the new 2.4 category at our Discussions site:
https://github.com/Security-Onion-Solutions/securityonion/discussions/categories/2-4
We welcome your detailed feedback!
Screenshot Tour