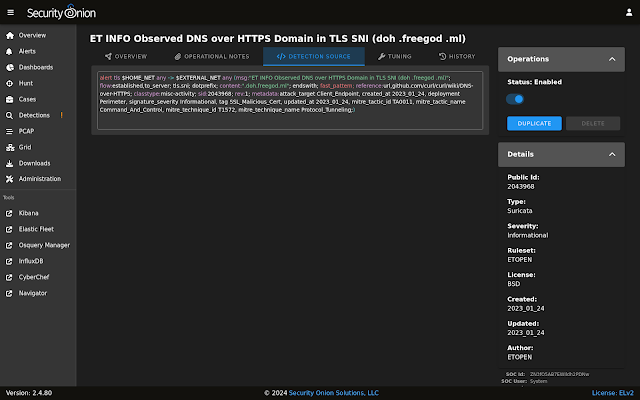
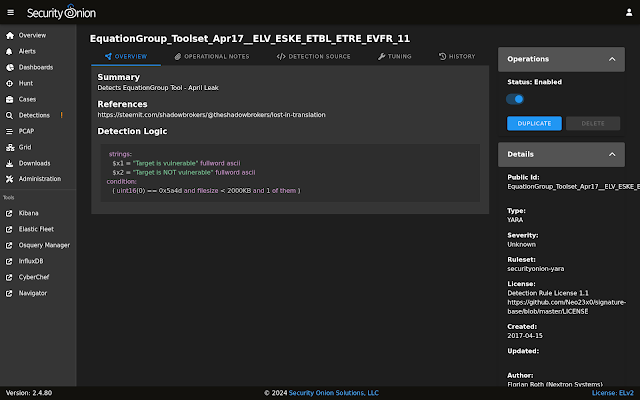
Since 2.4.70, we've listened to your feedback about Detections and made lots of improvements including syntax highlighting and much more!
We also continue to look for ways to help our fellow defenders when it comes to process logs. In previous versions, we added SOC actions for "Process Info" and "Process Ancestors". In this release, we've expanded on this with two more actions called "Process and Child Info" and "Process All Info":
Here's how these four process actions relate to each other:
- Clicking the Process Info option will show all logs that include this process’s entity_id in the process.entity_id field.
- Clicking the Process and Child Info option will show all logs that include this process’s entity_id in either the process.entity_id or process.parent.entity_id fields (depending on the process, this may show the same logs as the Process Info option or it may show more).
- Clicking the Process All Info option will show all logs that include this process’s entity_id in any field (depending on the process, this may show the same logs as the Process and Child Info option or it may show more).
- Clicking the Process Ancestors option will show all parent processes for the selected process.
Please note that these actions will only display on the Actions menu if you click on a specific log type:
- The first three Process actions will only appear if you click on a log that contains the process.entity_id field.
- The Process Ancestors action will only appear if you click on a log that contains the process.Ext.ancestry field.
There are many more features and fixes included in this release! For a complete list of all changes, please see the Release Notes:
https://docs.securityonion.net/en/2.4/release-notes.html#changes
Known Issues
For a list of known issues, please see:
https://docs.securityonion.net/en/2.4/release-notes.html#known-issues
About Security Onion
Security Onion is a free and open platform built by defenders for defenders. It includes network visibility, host visibility, intrusion detection honeypots, log management, and case management.
For network visibility, we offer signature based detection via Suricata, rich protocol metadata and file extraction using your choice of either Zeek or Suricata, full packet capture, and file analysis. For host visibility, we offer the Elastic Agent which provides data collection, live queries via osquery, and centralized management using Elastic Fleet. Intrusion detection honeypots based on OpenCanary can be added to your deployment for even more enterprise visibility. All of these logs flow into Elasticsearch and we’ve built our own user interfaces for alerts, dashboards, threat hunting, case management, and grid management.
Security Onion has been downloaded over 2 million times and is being used by security teams around the world to monitor and defend their enterprises. Our easy-to-use Setup wizard allows you to build a distributed grid for your enterprise in minutes!
Documentation
You can find our online documentation here:
https://docs.securityonion.net/en/2.4/
Documentation is always a work in progress. If you find documentation that needs to be updated, please let us know as described in the Feedback section below.
New Installations
If this is your first time installing Security Onion 2.4, then we highly recommend starting with an IMPORT installation as shown at:
https://docs.securityonion.net/en/2.4/first-time-users.html
Once you’re comfortable with your IMPORT installation, then you can move on to more advanced installations as shown at:
https://docs.securityonion.net/en/2.4/architecture.html
Existing 2.4 Installations
If you have an existing Security Onion 2.4 installation, you can update to the latest version using soup:
https://docs.securityonion.net/en/2.4/soup.html
Before updating your production deployment, we highly recommend testing the upgrade process on a test deployment that closely matches your production deployment if possible.
If you haven't already upgraded to 2.4.70 then, in preparation for the new Detections module, the following will be completed during soup:
- Playbook Plays will be backed up to /nsm/backup/detections-migration/ and any active Elastalert rules will be backed up and removed.
- Suricata tuning configurations will be backed to /nsm/backup/detections-migration/ and any thresholds will be migrated over to the new Detections module.
2.3 EOL
As a reminder, Security Onion 2.3 reached End Of Life (EOL) on April 6, 2024:
https://blog.securityonion.net/2023/10/6-month-eol-notice-for-security-onion-23.html
Thanks
Lots of love went into this release!
Special thanks to all our folks working so hard to make this release happen!
- Josh Brower
- Jason Ertel
- Wes Lambert
- Corey Ogburn
- Josh Patterson
- Mike Reeves
Questions, Problems, and Feedback
If you have any questions or problems relating to Security Onion 2.4, please use the 2.4 category at our Discussions site:
https://github.com/Security-Onion-Solutions/securityonion/discussions/categories/2-4
Coming Soon: Security Onion Pro
Next month, we plan to officially announce Security Onion Pro which includes many enterprise features that folks have been asking for:
- Open ID Connect (OIDC)
- Data at Rest Encryption
- FIPS for the OS
- DoD STIG for the OS
- External Notifications in SOC
- Time Tracking inside of Cases
- Guaranteed Message Delivery
You can read more about these enterprise features in the documentation:
https://docs.securityonion.net/en/2.4/pro.html
We'll provide more information next month, but if you'd like to go ahead and start a discussion with our sales team you can reach them using any of the contact forms at https://securityonionsolutions.com.
Training
Need training? Start with our free Security Onion Essentials training and then take a look at some of our other official Security Onion training!
https://securityonion.net/training
Security Onion Solutions Hardware Appliances
We know Security Onion's hardware needs, and our appliances are the perfect match for the platform. Leave the hardware research, testing, and support to us, so you can focus on what's important for your organization. Not only will you have confidence that your Security Onion deployment is running on the best-suited hardware, you will also be supporting future development and maintenance of the Security Onion project!
https://securityonionsolutions.com/hardware
Cloud Installations
For new Security Onion 2 installations in the cloud, Security Onion 2.4 will soon be available on the AWS, Azure, and GCP marketplaces!
AWS Marketplace and Documentation:
https://securityonion.net/aws/?ref=_ptnr_soc_blog_240529
https://docs.securityonion.net/en/2.4/cloud-amazon.html
Azure Marketplace and documentation:
https://securityonion.net/azure
https://docs.securityonion.net/en/2.4/cloud-azure.html
GCP Marketplace and documentation:
https://securityonion.net/google
https://docs.securityonion.net/en/2.4/cloud-google.html
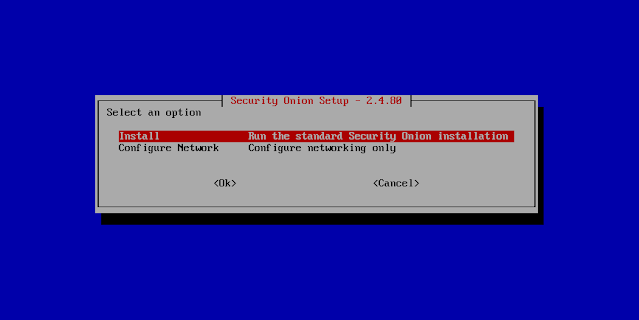
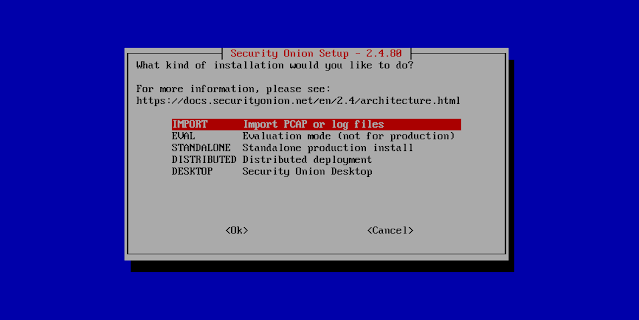
Screenshot Tour
If you want the quickest and easiest way to try out Security Onion 2.4, just follow the screenshots below to install an Import node. This can be done in a minimal VM with only 4GB RAM! For more information, please see:
https://docs.securityonion.net/en/2.4/first-time-users.html