We hope your 2022 is off to a great start! We're excited for what this year will bring, starting with two major changes coming very soon!
High Availability Pipeline via New Receiver Node
Our customers and community have asked for a high availability pipeline option and so we are happy to announce that Security Onion 2.3.100 will include a new role option called the “receiver node.” This node allows for redundancy in the data pipeline so if for some reason the manager goes down the search nodes can continue to receive data. This also allows for load balancing of external log sources if the manager is overloaded.
Say Goodbye to TheHive and Hello to Cases!
In September, 2021, StrangeBee announced a change to TheHive's licensing model and ended support for TheHive version 3 effective December 31, 2021:
https://medium.com/strangebee-announcements/faq-for-thehive-5s-upcoming-distribution-model-af0ccb95d18
The new licensing model for TheHive version 5 is not compatible with our project so we must say goodbye to TheHive and Cortex. With the release of Security Onion 2.3.100, existing installations with TheHive enabled will still be able to use TheHive for a very short time. However, new installations will not be able to enable TheHive. We will stop including TheHive and Cortex container images starting in Security Onion 2.3.120, currently scheduled for release in March 2022. From that point forward, users running the current version of Security Onion will no longer be able to natively run TheHive on the platform and our support for TheHive on Security Onion will end. Users wishing to continue using TheHive on Security Onion should plan to migrate to an external instance of TheHive. For now, users will still be able to escalate events from Security Onion Console to external instances of TheHive version 3.
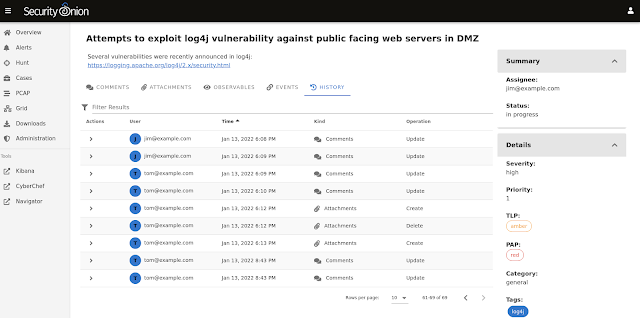
We took this opportunity to re-imagine case management. We started with standard case management features:
- assigning analysts
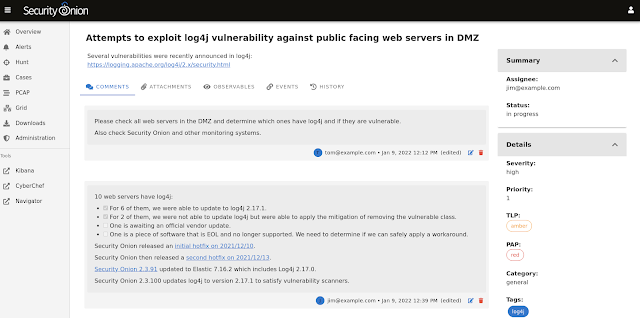
- defining Severity, Priority, TLP, PAP, Category, and Tags
- robust commenting including markdown support
- adding attachments
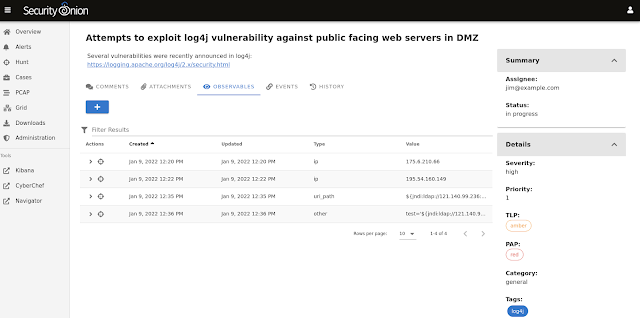
- tracking observables
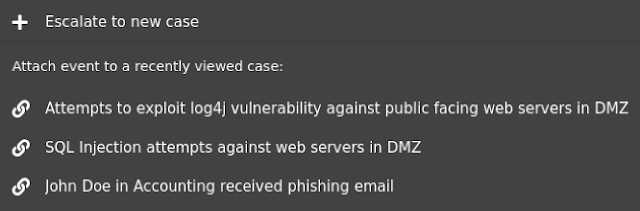
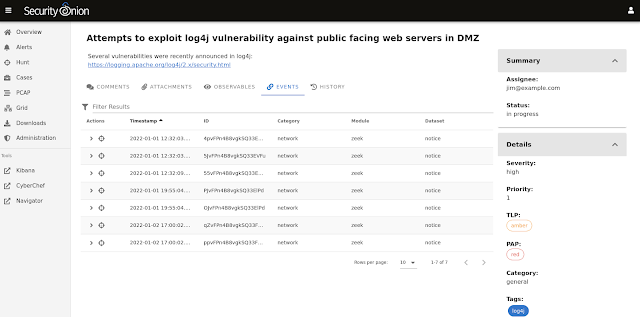
Now what if all of these features were even more tightly integrated into Security Onion Console? What if users could go to the Alerts page and escalate multiple alerts to the same case quickly and easily without having to merge cases? What if they could then pivot to the Hunt interface to find related logs and add those to the same case just as quickly and easily?
We are excited to announce that Security Onion 2.3.100 will include SOC Cases! For more information, please see the screenshot tour below and the documentation at:
https://docs.securityonion.net/en/2.3/cases.html
Stay tuned for Security Onion 2.3.100 and SOC Cases!
Questions
If you have any questions about any of these changes, please start a new discussion at:
https://securityonion.net/discuss
Screenshot Tour