Today, the FBI and DOJ announced an operation to dismantle Qakbot infrastructure:
https://www.fbi.gov/news/stories/fbi-partners-dismantle-qakbot-infrastructure-in-multinational-cyber-takedown
https://www.justice.gov/usao-cdca/pr/qakbot-malware-disrupted-international-cyber-takedown
Let's take a look at a recent Qakbot sample. Thanks to Brad Duncan for sharing this pcap:
https://www.malware-traffic-analysis.net/2023/05/24/index.html
We did a quick analysis of this pcap on the NEW Security Onion 2.4. If you'd like to follow along, you can install Security Onion 2.4 in a VM and import the pcap using so-import-pcap:
https://docs.securityonion.net/en/2.4/first-time-users.html
https://docs.securityonion.net/en/2.4/so-import-pcap.html#so-import-pcap
The screenshots at the bottom of this post show some of the interesting NIDS alerts, metadata logs, and session transcripts. Want more practice? Check out our other Quick Malware posts at:
https://blog.securityonion.net/search/label/quick%20malware%20analysis
About Security Onion
Security Onion is a versatile and scalable platform that can run on small virtual machines and can also scale up to the opposite end of the hardware spectrum to take advantage of extremely powerful server-class machines. Security Onion can also scale horizontally, growing from a standalone single-machine deployment to a full distributed deployment with tens or hundreds of machines as dictated by your enterprise visibility needs. To learn more about Security Onion, please see https://securityonion.net.
Our 10th Annual Security Onion Conference is coming up soon! Reserve your seat today! Last day to register is September 29! For more details, please see https://socaugusta2023.eventbrite.com/.
Do you want to deploy the new Security Onion 2.4 to your enterprise but need training? Our first 4-day public training class on Security Onion 2.4 will be in beautiful Augusta GA as part of Augusta Cyber Week! The class is at a very special price AND you get a free ticket to BOTH Security Onion Conference AND BSidesAugusta! For more information, please see https://blog.securityonion.net/2023/07/registration-now-open-for-augusta-cyber.html.
Do you want to deploy Security Onion to your enterprise and want the best enterprise hardware? We know Security Onion's hardware needs, and our appliances are the perfect match for the platform. Leave the hardware research, testing, and support to us, so you can focus on what's important for your organization. Not only will you have confidence that your Security Onion deployment is running on the best-suited hardware, you will also be supporting future development and maintenance of the Security Onion project! For more information, please see https://securityonionsolutions.com/hardware.
Screenshots
First, we start with the overview of all alerts and logs:
Next, let's review the alerts:
When we pivot from the EXE alert to the PCAP transcript, we notice that the HTTP request is to a bare IP address instead of a fully qualified domain name, the file requested is a .dat file, and the file returned has the standard MZ file header of an EXE:
Next, let's review all of the network protocol metadata:
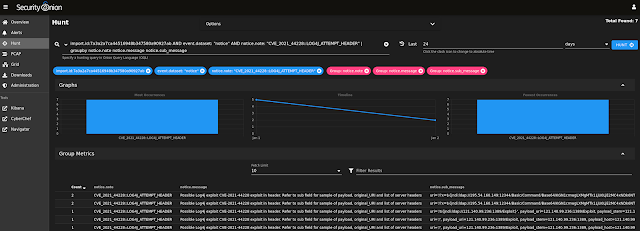
Drilling into the Zeek Notices, we see an interesting connection on port 2222:
Here are the SSL/TLS logs including that port 2222 connection noted in the previous screenshot:
Here is an overview of all connections:
Drilling into HTTP logs we notice that, in addition to the EXE that we looked at earlier, there was a ZIP download:
Pivoting on that file transfer, we see the PK file header and that the embedded file appears to be called Claim_A615.wsf:
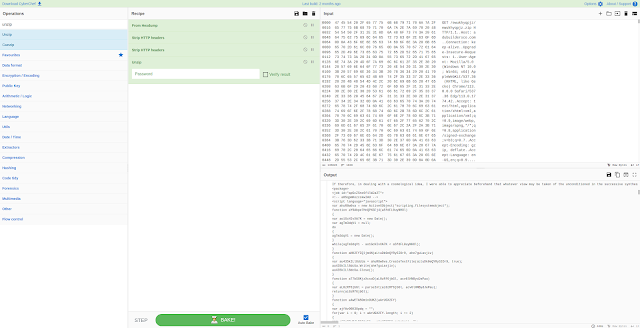
From there, we pivot to CyberChef and carve the WSF (Windows Script File):
The top of the file seemed innocent enough, but as we scroll down we see something more nefarious: