This security advisory only applies to Security Onion Elastic Alpha. If you're running the stable version of Security Onion (ELSA instead of Elastic), this does not apply to you. Since this advisory only applies to Security Onion Elastic Alpha, please be reminded of the usual warnings and disclaimers:
- Experimental Setup is ALPHA, BLEEDING EDGE, and TOTALLY UNSUPPORTED!
- If this breaks your system, you get to keep both pieces!
- This is a work in progress and is in constant flux.
- This is intended to build a quick prototype proof of concept so you can see what our ultimate Elastic configuration might look like. This configuration will change drastically over time leading up to the final release.
- Do NOT run this on a system that you care about!
- Do NOT run this on a system that has data that you care about!
- This should only be run on a TEST box with TEST data!
- Experimental Setup may result in nausea, vomiting, or a burning sensation.
Introduction
Security Onion Elastic Alpha runs the Elastic stack (Elasticsearch, Logstash, and Kibana). UFW, the host-based firewall, is configured to only allow connections to port 22 by default. Apache is configured as a proxy to authenticate users before accessing Kibana. Therefore, the original intention of the design was that a user would run Setup and then run so-allow to allow their workstation IP to connect over the network to port 443 where Apache was proxying Kibana and requiring authentication. However, due to incorrect Docker parameters, Kibana and Elasticsearch ports were being published directly to the network allowing users to bypass both the UFW firewall and the Apache proxy and access Kibana and Elasticsearch directly with no authentication. This has been corrected in the lastest securityonion-elastic package (securityonion-elastic - 20171011-1ubuntu1securityonion1).
Resolution
If you're running the stable version of Security Onion (ELSA instead of Elastic), there is nothing to do.
If you're running Security Onion Elastic Alpha and you've already run Setup, please run the following:
sudo soupIf you haven't yet run Setup and are planning to choose the Experimental option to enable the Elastic stack, just make sure that you run "sudo soup" before running Setup.
sudo so-elastic-restart
Discussion
Previously, our so-elastic-start script would start containers using a --publish parameter like this (in the case of Kibana):
--publish 5601:5601
If you were to then examine the host-based firewall configuration, you would see that only port 22 is open by default:
 |
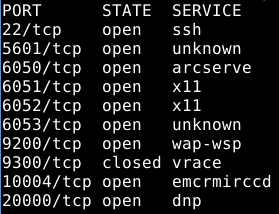
However, if you were to port scan the box remotely, you would see more than port 22 open:
Now let's install the new securityonion-elastic package (securityonion-elastic - 20171011-1ubuntu1securityonion1):
sudo soup
This new package starts containers using a --publish parameter that only publishes to localhost like this (in the case of Kibana):
--publish 127.0.0.1:5601:5601
securityonion-elastic - 20171011-1ubuntu1securityonion1 makes the following changes:
- so-kibana publishes port 5601 to 127.0.0.1 only
- so-elasticsearch publishes ports 9200 and 9300 to 127.0.0.1 only
- so-logstash publishes ports 6050, 6051, 6052, and 6053 to 127.0.0.1 only
- so-freqserver no longer publishes port 10004
- so-domainstats no longer publishes port 20000
Now we need to restart the Docker containers:
sudo so-elastic-restart
Finally, we re-run the remote port scan to verify that only port 22 is open:
More Information
For more information, please see:
http://blog.viktorpetersson.com/post/101707677489/the-dangers-of-ufw-docker
https://github.com/moby/moby/issues/4737
Thanks
Special thanks to Todd Carlson for responsibly disclosing this security issue per our Security page:
https://securityonion.net/security
Timeline
All times below are in Eastern time.
10/10/2017 10:02 PM - Received initial notification from Todd Carlson.
10/11/2017 8:35 AM - Confirmed receipt of email, confirmed issue, and committed initial fix.
10/11/2017 9:52 AM - Built new securityonion-elastic package and asked Todd to test and confirm.
10/12/2017 8:18 PM - Received confirmation from Todd that the new package resolved the issue.
10/16/2017 7:20 AM - Pushed new securityonion-elastic package to stable repo.

No comments:
Post a Comment