Thanks to Brad Duncan for sharing this pcap from 2024-09-17 on his malware traffic analysis site! Due to issues with Google flagging a warning for the site, we're not including the actual hyperlink but it should be easy to find.
We did a quick analysis of this pcap on the NEW Security Onion 2.4.100:
https://blog.securityonion.net/2024/08/security-onion-24100-now-available.html
If you'd like to follow along, you can do the following:
The screenshots at the bottom of this post show some of the interesting alerts, metadata logs, and session transcripts. Want more practice? Check out our other Quick Malware Analysis posts at:
https://blog.securityonion.net/search/label/quick%20malware%20analysis
About Security Onion
Security Onion is a versatile and scalable platform that can run on small virtual machines and can also scale up to the opposite end of the hardware spectrum to take advantage of extremely powerful server-class machines. Security Onion can also scale horizontally, growing from a standalone single-machine deployment to a full distributed deployment with tens or hundreds of machines as dictated by your enterprise visibility needs. To learn more about Security Onion, please see:
https://securityonion.net
Screenshots
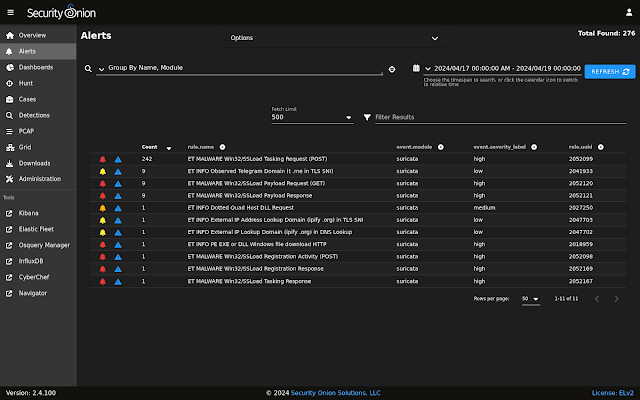
First, we start with the overview of all alerts and logs:
Next, we look at just the NIDS alerts generated by Suricata:
Let's drill into the Snake keylogger alert:
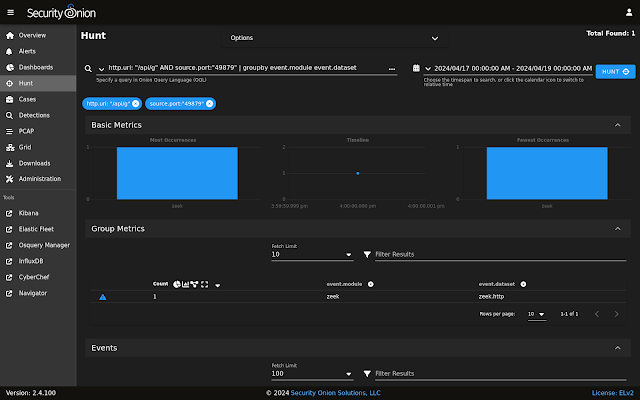
This looks interesting so let's pivot to PCAP:
We can switch to ASCII transcript to make it more readable:
Now let's review the protocol metadata provided by Zeek:
We start with the Software dashboard where we see an interesting browser user agent string:
Next, let's review the X.509 dashboard:
and the associated SSL/TLS dashboard:
Next, we'll look at the DNS dashboard:
Looking at the HTTP dashboard, we see the interesting browser user agent we saw earlier on the Software dashboard:
Looking at the Files dashboard, we can see files being transferred by both HTTP and FTP:
Let's review the FTP dashboard. Here we see a couple of files being transferred:
At the bottom of the FTP dashboard, we can see the 2 FTP STOR transactions where files are being exfiltrated:
If we pivot to PCAP, we can see the FTP CONTROL channel:
To see the FTP DATA channel, we can switch to the Connections dashboard:
Pivoting to PCAP, we see one of the exfil files contains the user's browser cookies:
And the second exfil file contains the user's saved passwords: