Thanks to Brad Duncan for sharing this pcap!
https://www.malware-traffic-analysis.net/2022/09/29/index.html
We did a quick analysis of this pcap on the latest version of Security Onion via so-import-pcap:
https://docs.securityonion.net/en/2.3/so-import-pcap.html
The screenshots below show some of the interesting Suricata alerts, Zeek logs, and session transcripts. We start with NIDS alerts from the Emerging Threats Open ruleset and then pivot to the full TCP stream for interesting alerts. We then look at protocol metadata provided by Zeek such as HTTP transactions and DNS lookups. We go through each protocol and look at an overview of all logs for that data type.
About Security Onion
Security Onion is a versatile and scalable platform that can run on small virtual machines and can also scale up to the opposite end of the hardware spectrum to take advantage of extremely powerful server-class machines. Security Onion can also scale horizontally, growing from a standalone single-machine deployment to a full distributed deployment with tens or hundreds of machines as dictated by your enterprise visibility needs.
To learn more about Security Onion, please see:
https://securityonion.net
https://securityonion.net/docs
More Samples
Find all of our Quick Malware posts at:
https://blog.securityonion.net/search/label/quick%20malware%20analysis
Screenshots
Click the first image to start the screenshot tour:
 |
| Suricata NIDS Alerts |
 |
| Pivoting from NIDS alert to full TCP stream |
 |
| TCP stream for first alert |
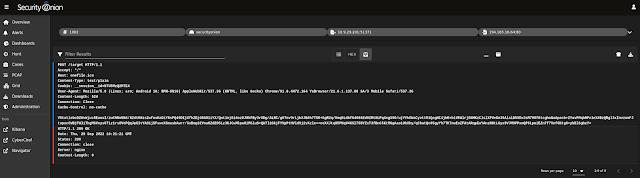 |
| TCP stream for second alert |
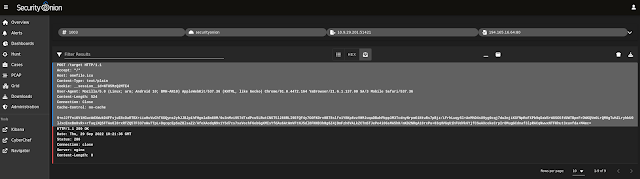 |
| TCP stream for third alert |
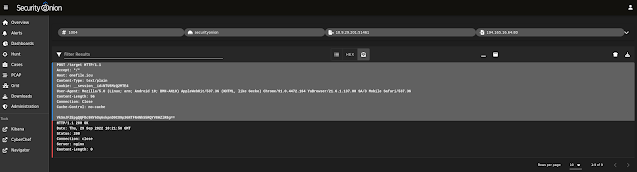 |
| TCP stream for fourth alert |
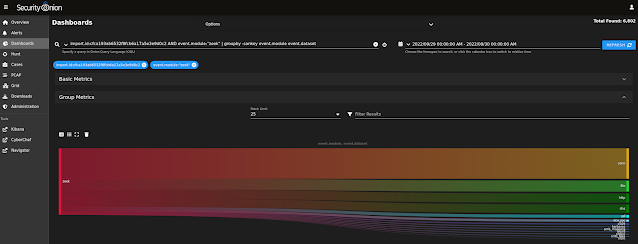 |
| Overview of all Zeek protocol metadata |
 |
| NTLM metadata |
 |
| smb_files metadata |
 |
| Zeek Notice logs |
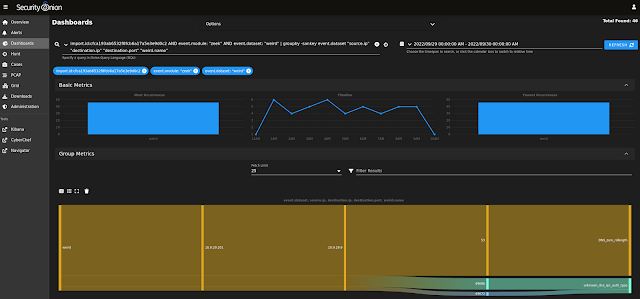 |
| Zeek Weird logs |
 |
| SMB mapping metadata |
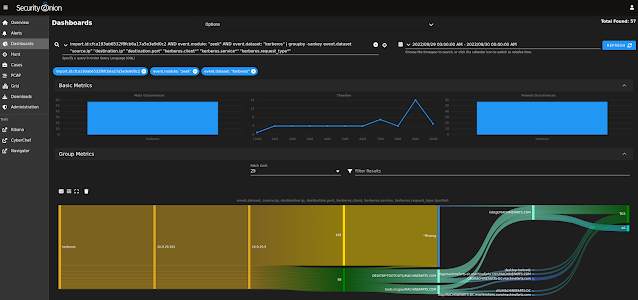 |
| Kerberos metadata |
 |
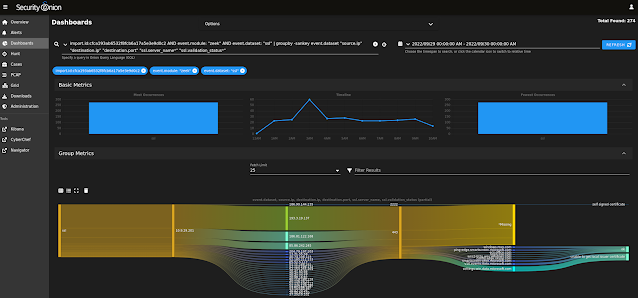
| X.509 metadata |
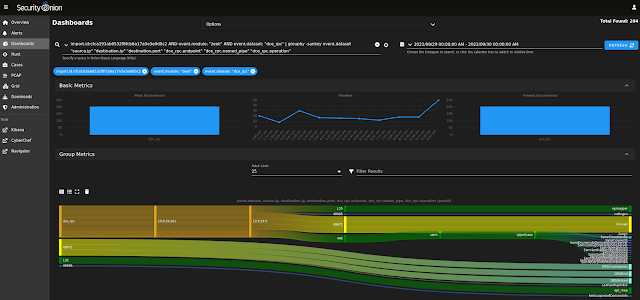 |
| DCE_RPC metadata |
 |
| SSL metadata |
 |
| DNS lookups |
 |
| HTTP transactions |
 |
| Interesting connections |
No comments:
Post a Comment
Note: Only a member of this blog may post a comment.