Disclaimer: I offer no warranties of any kind. If your box breaks, you get to keep both pieces!
Step 1: Get root privileges
##########################Step 2: Install NSMnow
sudo -i
##########################
##########################Step 3: Configure AppArmor and start NSMnow
mkdir /usr/local/src/NSMnow
cd /usr/local/src/NSMnow
wget http://www.securixlive.com/download/nsmnow/NSMnow-1.4.0.tar.gz
tar zxvf NSMnow-1.4.0.tar.gz
./NSMnow -i -y
##########################
##########################Snort is now capturing packets on eth0 and analyzing them. Let's verify that now.
if ! grep "/nsm/server_data/server1/load" /etc/apparmor.d/usr.sbin.mysqld > /dev/null
then
# Remove the last line of the file (a single right curly brace)
sed -i '$d' /etc/apparmor.d/usr.sbin.mysqld
# Add a line that allows MySQL to read the load directory
echo " /nsm/server_data/server1/load/* r," >> /etc/apparmor.d/usr.sbin.mysqld
# Append the right curly brace to end the file
echo "}" >> /etc/apparmor.d/usr.sbin.mysqld
fi
if ! grep "/nsm/sensor_data/sensor1/dailylogs" /etc/apparmor.d/usr.sbin.tcpdump > /dev/null
then
# Remove the last line of the file (a single right curly brace)
sed -i '$d' /etc/apparmor.d/usr.sbin.tcpdump
# Add a line that allows tcpdump to read all dailylogs
echo " /nsm/sensor_data/sensor1/dailylogs/**[^/] r," >> /etc/apparmor.d/usr.sbin.tcpdump
echo "}" >> /etc/apparmor.d/usr.sbin.tcpdump
fi
/etc/init.d/apparmor restart
/usr/local/sbin/nsm --all --start
##########################
Launch the Sguil client by opening a new terminal and typing the following:
##########################When prompted, login to Sguil using the default credentials:
sguil.tk
##########################
Username: sguil
Password: password
Next, create some alerts by opening a browser and going to:
http://www.testmyids.com
Finally, go into the Sguil console and you should see two new alerts:
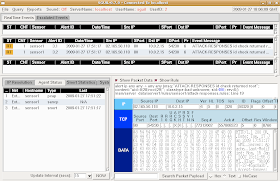
This demonstrates that Snort is analyzing packets and outputting in unified2 format, which is then read by Barnyard2 and inserted into the Sguil database.
When finished, close the Sguil window and return to your NSMnow window. Then type the following to terminate all NSMnow processes:
/usr/local/sbin/nsm --all --stop
No comments:
Post a Comment
Note: Only a member of this blog may post a comment.