Please note that if you have an existing NSMnow installation, following this recipe may or may not work. This recipe is designed for new NSMnow installations.
The best open source tool to manage Snort alerts is Sguil and the easiest way to install Sguil is using NSMnow. NSMnow automatically installs and configures barnyard2 (compatible with SnortSP's unfied2 format), sancp, Sguil, and Snort 2.x. We're going to replace NSMnow's snort alert process with Snort 3.0.
This quick recipe assumes that you're running on Ubuntu 8.04 and your primary network interface is eth0. You should be able to copy/paste each of the three code blocks into your terminal.
Obligatory disclaimer: I offer no warranty of any kind. If this breaks your box, you get to keep both pieces.
Step 1: Get root privileges
##########################Step 2: Install NSMnow
sudo -i
##########################
##########################Step 3: Configure NSMnow and SnortSP and start
mkdir /usr/local/src/NSMnow
cd /usr/local/src/NSMnow
wget http://www.securixlive.com/download/nsmnow/NSMnow-1.3.5.tar.gz
tar zxvf NSMnow-1.3.5.tar.gz
./NSMnow -i -y
##########################
##########################Snort 3.0 is now capturing packets on eth0 and analyzing them. Let's verify that now.
if ! grep "/nsm/server_data/server1/load" /etc/apparmor.d/usr.sbin.mysqld > /dev/null
then
sed -i 's|}| /nsm/server_data/server1/load/* r,|g' /etc/apparmor.d/usr.sbin.mysqld
echo "}" >> /etc/apparmor.d/usr.sbin.mysqld
fi
/etc/init.d/apparmor restart
/usr/local/sbin/nsm --server --start
/usr/local/sbin/nsm_sensor_ps-start --skip-snort-alert
mkdir /etc/snortsp_alert
cd /etc/snortsp_alert
cp -R /etc/nsm/sensor1/* .
mv snort.conf snort_orig.conf
sspiffy.sh /usr/local -c snort_orig.conf -i eth0
sed -i 's|type="file"|type="pcap"|g' snort.lua
grep -v "sameip" rules/bad-traffic.rules > rules/bad-traffic.rules.2
rm -f rules/bad-traffic.rules
mv rules/bad-traffic.rules.2 rules/bad-traffic.rules
snortsp -C -L snort.lua
##########################
Launch the Sguil client by opening a new terminal and typing the following:
##########################When prompted, login to Sguil using the default credentials:
sguil.tk
##########################
Username: sguil
Password: password
Next, create some alerts by opening a browser and going to:
http://www.testmyids.com
Finally, go into the Sguil console and you should see two new alerts:
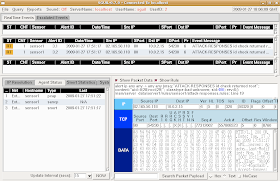
This demonstrates that SnortSP is capturing packets, analyzing them with the Snort 2.8.2 Detection Engine, and outputting in unified2 format, which is then read by Barnyard2 and inserted into the Sguil database.
When finished, return to your SnortSP window and press ctrl-c to terminate the SnortSP process. Then type "nsm --all --stop" to terminate all NSMnow processes.
I might be mistaken but NSMnow is installing snort 2 and not snort 3.0 beta 3
ReplyDeleteAnonymous,
ReplyDeleteYou are correct--NSMnow installs Snort 2 and not Snort 3.0 Beta 3. This procedure assumes that you have already installed Snort 3.0 Beta 3 per my instructions here:
http://securityonion.blogspot.com/2009/04/installing-snort-30-snortsp-beta-3-on.htmlNSMnow is then used to automatically install and configure Sguil and its components. The remaining steps then configure Snort 3.0 Beta 3 to replace NSMnow's Snort 2 alert process.
For more detailed information, please reference my SANS GCIA Gold paper:
http://www.sans.org/reading_room/whitepapers/detection/snort_3_0_beta_3_for_analysts_33068Please let me know if you have any further questions or problems.
Thanks,
Doug Burks
http://securityonion.blogspot.com
Doug i downloaded the tar file for NSMnow not the administration part, i untarred it and it is asking me this: PAth where all downloaded files will be saved what is the best place for them?
ReplyDeletedoug, now after i installed the NSM tar with all the programs, i went thru the yes or no and default questions, i gave mysql a root password and so forth well i did this command just to test liek teh website says: nsm --all --start
ReplyDeleteand it comes up with a lot of stuff and at the end though it says this?
Starting: cu
* starting: pcap_agent (sguil) [ OK ]
* starting: sancp_agent (sguil) [ OK ]
* starting: snort_agent (sguil) [ OK ]
* starting: snort (alert data) [ OK ]
* starting: barnyard2 (spooler, unified2 format) [ OK ]
* starting: sancp (session data)Usage: grep [OPTION]... PATTERN [FILE]...
Try `grep --help' for more information.
[ FAIL ]
- check /var/log/nsm/cu/sancp.log for error messages
* starting: snort (full packet data)Usage: grep [OPTION]... PATTERN [FILE]...
Try `grep --help' for more information.
[ FAIL ]
- check /var/log/nsm/cu/snortl.log for error messages
* disk space currently at 10%
is this soemthing to worry about?
sorry i am intermediate and still learning linux and snort.
thanks for your help
JTB,
ReplyDeleteI've never seen that issue before. You are running a fully patched Ubuntu 8.04, right? You might try starting over and using the following command to install NSMnow:
./NSMnow -i -y
This will accept all default configuration, which is what I normally do. If you still have the problem, you might try contacting the NSMnow developers at http://www.securixlive.com. They are usually very quick to respond.
Please let me know how it goes.
Thanks,
Doug Burks
Thanks Doug will do quick ?
ReplyDeletehave u seen this:
Checking for corrupt, not cleanly closed and upgrade needing tables.
[2009/05/06 10:31:35] #1 - Configuring package: tcl
[2009/05/06 10:31:35] #1 - Configuring package: buildessential
[2009/05/06 10:31:35] #1 - Configuring package: snort
[2009/05/06 10:31:35] #1 - snort source is NOT available
ERROR: snort unable to be configured.
i installed like you said but i get this error at the end of the install.
JTB,
ReplyDeleteI haven't seen that issue before. Did you start over from a fresh install of Ubuntu 8.04, or was your previous NSMnow installation in place? If your previous NSMnow installation was in place, you can try using the NSMnow uninstaller, but I've had mixed results with it in the past. The easiest option is to start with a fresh Ubuntu 8.04 installation (this is when virtual machine snapshots come in handy). If all else fails, please contact the NSMnow developers for assistance.
Thanks,
Doug Burks